How PoW blockchain Works
Proof-of-Work is the first consensus algorithm. It was developed by Satoshi Nakamoto back in 2008, and lies at the core of the Bitcoin network.
Proof-of-Work is a mechanism for achieving consensus through proof of expended effort. It involves mining — performing mathematical computations to create new blocks.
In contrast to TradFi, blockchains do not have centralized servers or departments to verify transactions. Miners, or more precisely, their computers, take on this function. They solve cryptographic tasks, confirm transfers, and record data in the blockchain, thereby creating a new block.
Powerful mining farms are required to solve these tasks, the assembly of which can cost thousands of dollars.
A powerful ASIC for Bitcoin mining, such as the Antminer S19 XP 140 Th/s, sells for a minimum of $2,800. Even one such device is insufficient to ensure a good income.
The feature of Proof-of-Work is that the complexity of the cryptographic task increases with the hash rate. The more computers are connected to the network, the more computations are required. This makes attacks on powerful blockchains close to impossible and unprofitable.
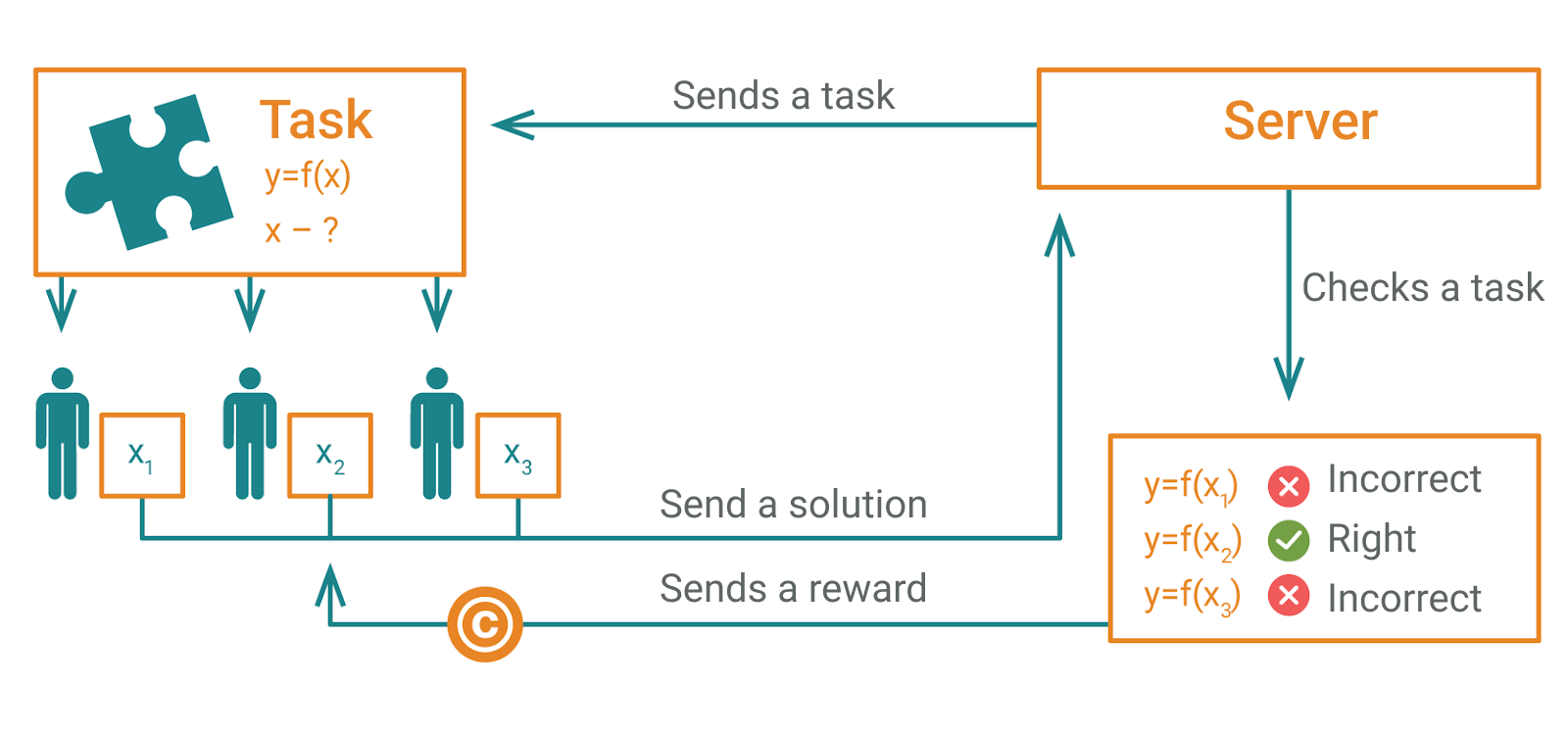
Transaction Cycle in the blockchain
Confirmation of transfers and data storage occurs in five steps:
1. The user transfers coins from their wallet to another.
2. Information about the transaction is recorded in the Mempool (a shared ledger).
3. The blockchain creates algorithms to verify input and output data.
4. Miners connected to the network solve a cryptographic task. The one who first finds the key gets the opportunity to verify the transaction and add it to a new block.
5. If everything is correct, information about the transaction is recorded into the block, and the user receives a reward.
The speed of solving the task depends on two factors: the network’s hash rate and the mining farm itself. The higher the first indicator, the more numbers need to be processed. That is why there is an “arms race” among Bitcoin miners.
How Cryptographic Riddles are Solved
In essence, such a task involves simple number crunching. Initially, the blockchain algorithm creates a hash sum and sets a minimum value boundary. Mining farms start recalculating each digit in the combination. If the resulting hash sum matches, the task is considered solved. Otherwise, the technique continues iterating.
It’s impossible to solve such a combination without powerful equipment. There’s no pattern allowing for a quick determination of the correct hash sum. The only way to perform computations faster and earn rewards for block discovery is to expand the farm.
Typically, blocks are mined by large farms and pools, as they have the power for quick task resolution. However, occasionally solo miners manage to mine an entire block. Such occurrences are extremely rare, so relying on them isn’t advisable.
Hashing Algorithms with PoW
Hashing algorithms differ in their encryption mechanism and security provision. Currently, in PoW blockchains, five algorithms are most commonly encountered:
- SHA-256 — generates a unique 256-bit hash function of a fixed size for each block. According to the algorithm’s creator, it would take over 1 million years to crack on a home PC. SHA-256 is used in Bitcoin. It’s not recommended to mine it on GPU or CPU, as such networks are almost entirely dominated by high-performance ASICs;
- Scrypt — essentially similar to SHA-256, but developers reduced ASIC efficiency to allow GPU mining. However, as of 2023, ASICs optimized for this algorithm can be found, significantly affecting the profitability of home mining depending on the hash rate and industrial miners’ interest;
- CryptoNight — an ASIC-resistant algorithm. CryptoNight is used for mining coins that support the CryptoNote protocol, including Monero. It heavily relies on memory (memory hard hash), specifically the third-level cache memory of processors, as it’s oriented toward delay;
- Ethash — created as a function for Ethereum blockchain’s proof-of-work verification. This algorithm combines two standard cryptographic functions, SHA-3 and Keccak, resulting in a function resistant to ASIC but fast in verification and execution;
- X11 — successor to variants X13, X15, and X17. It’s a proof-of-work algorithm designed for high efficiency on both CPU and GPU. It employs a combination of eleven different encryption algorithms.
If you plan to mine using graphics cards, choose blockchains with ASIC resistance. This term refers to the algorithm’s feature of artificially reducing the hash rate, making home farms competitive.
How Cryptocurrency is Mined
Mining is the process of acquiring digital coins. Although the equipment continuously performs complex calculations, the user doesn’t need to do much. It’s enough to purchase the equipment, connect it, and set it up. Because of this, mining is often referred to as a passive source of income.
In reality, it’s a bit more complicated, as it’s not like a bank deposit where you can forget about it for a couple of years while the interest accumulates. You’ll need to constantly monitor the state of the farm and search for new digital assets.
By solving cryptographic tasks and creating blocks in the chain, a miner receives coins frozen within the system. Only one user, the first to complete the hash-sum calculation, receives them.
Because of this, a race involving a constant purchase of new equipment and expansion of farms has begun.
Is PoW Really Secure, and what is the 51% Attack
Initially, blockchain was created as an analogue of centralized bank networks. Hack it and get all the depositors’ money. At first, this was the case, but the growing hash rate forced miners to gather in pools.
This led to the centralization of power in the hands of a few individuals — the creators of the pools.
The essence of the 51% attack is that attackers gain access to 51% of the hash rate. This allows them to counterfeit blocks and spend cryptocurrency twice.
Previously affected by it:
- Monacoin;
- Bitcoin Gold;
- Litecoin Cash;
- ZenCash.
In the case of Bitcoin, this threat has little chance of realization, as seizing such a volume of hash rate would require an incredible amount of equipment. The larger the blockchain grows, the less likely it is to encounter a 51% attack. Therefore, only small blockchains have suffered from it so far.
